SOC 2 Compliance: An Overview of What Your Business Needs to Know
No matter the business size, the threat of data breaches or hacks is a dark cloud that hangs over every company. If data is mishandled, leaked, or stolen, the repercussions for businesses can be devastating.
Cyberattacks on businesses can cause severe financial losses due to fines, legal fees, and remediation costs. As businesses are legally obliged to inform customers of a data breach, once customers find out, they can also cause irreparable damage to reputation, customer distrust, and loss of business.
Additionally, companies may face regulatory penalties, increased insurance premiums, and operational disruptions that impact productivity and business continuity, begging the question, what can businesses do to prevent this?
One of many solutions is SOC 2 compliance. SOC 2, or Service Organization Control 2, is a framework designed to help organizations manage and safeguard customer data by adhering to strict security standards.
This article will outline how SOC 2 can benefit your business's risk management, meet compliance standards, and improve your organization's security program.
Table of contents
- Internxt Drive: Security
- Internxt Drive: Availability
- Internxt Drive: Processing Integrity
- Internxt Drive: Privacy
- Internxt Drive: Points of Focus
- Internxt Business Plans
- Internxt Object Storage
What is SOC 2?
SOC 2 stands for Service Organization Control 2. It is a framework developed by the American Institute of CPAs (AICPA) to help organizations manage and protect data. SOC 2 involves a report demonstrating a strong control environment, achieved through an independent third-party auditor (CPA) audit.
Risk management must also extend to third parties to ensure they have effective information security and can minimize security risks. SOC 2 is used to audit the security practices of third-party vendors to confirm they meet the protection standards required by your organization.
The SOC 2 framework
The SOC 2 framework is widely used by service organizations, especially SaaS companies, due to its flexibility
SOC 2 allows organizations to customize how they implement security controls if they meet the criteria and effectively address privacy risks. We will look at this next.
What are the requirements for SOC 2?
SOC 2 compliance requires organizations to meet specific security criteria based on the Trust Service Criteria, which are grouped into five principles.
A SOC 2 audit assesses the controls and framework that enable an organization to meet compliance standards; the report monitors whether an organization can meet some or all of these five trust service principles.
Security
Security monitors systems to ensure they are protected against unauthorized access, disclosure, and damage to information that could compromise its availability, integrity, confidentiality, and privacy.
Security is included in every SOC 2 report, and organizations can opt only to be examined on security controls that fall under the security principle, some of which are:
- Organizational structure
- Endpoint security
- User security awareness
- Firewall and risk management
- Identity access, and authentication management
- Data security and center control (if applicable)
Availability
Availability confirms that all systems are available and perform as expected based on service level agreements. It also includes regular maintenance and updates to ensure they can continue to function properly.
To maintain system availability during disruptions, companies must show they can implement and test disaster recover plans.
Processing Integrity
To ensure data accuracy, make sure that all data processing is correct, complete, and authorized. Implement procedures to detect and fix any errors that occur during data processing. Additionally, controls must be established to guarantee that systems process data as intended.
Confidentiality
This ensures that the necessary access controls and data handling regulations protect confidential information.
Privacy
This addresses how personal information is collected, used, retained, and disclosed. In this case, confidentiality refers to sensitive information, and privacy applies to personal information.
Personal information must be managed according to privacy policies, consent must be obtained from individuals to provide information on how data will be used, and policies must be established for the retention and secure disposal of personal data.
Points of Focus
Points of Focus are included in a SOC 2 report to add detailed aspects for more context and clarity on how your organization meets the Trust Services Criteria.
Points of Focus help auditors and stakeholders understand the controls and practices an organization has implemented to address the criteria of Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Below are examples of use cases for Trust Services
Organizations should prepare to explain to SOC 2 auditors why certain Trust Services Criteria are not relevant to their criteria. This usually happens when the activity is separate from the organization's criteria or is handled by a third party.
In this case, the SOC 2 report may exclude those specific criteria from the audit scope. This allows the report to accurately reflect the areas where the organization is not responsible or involved.
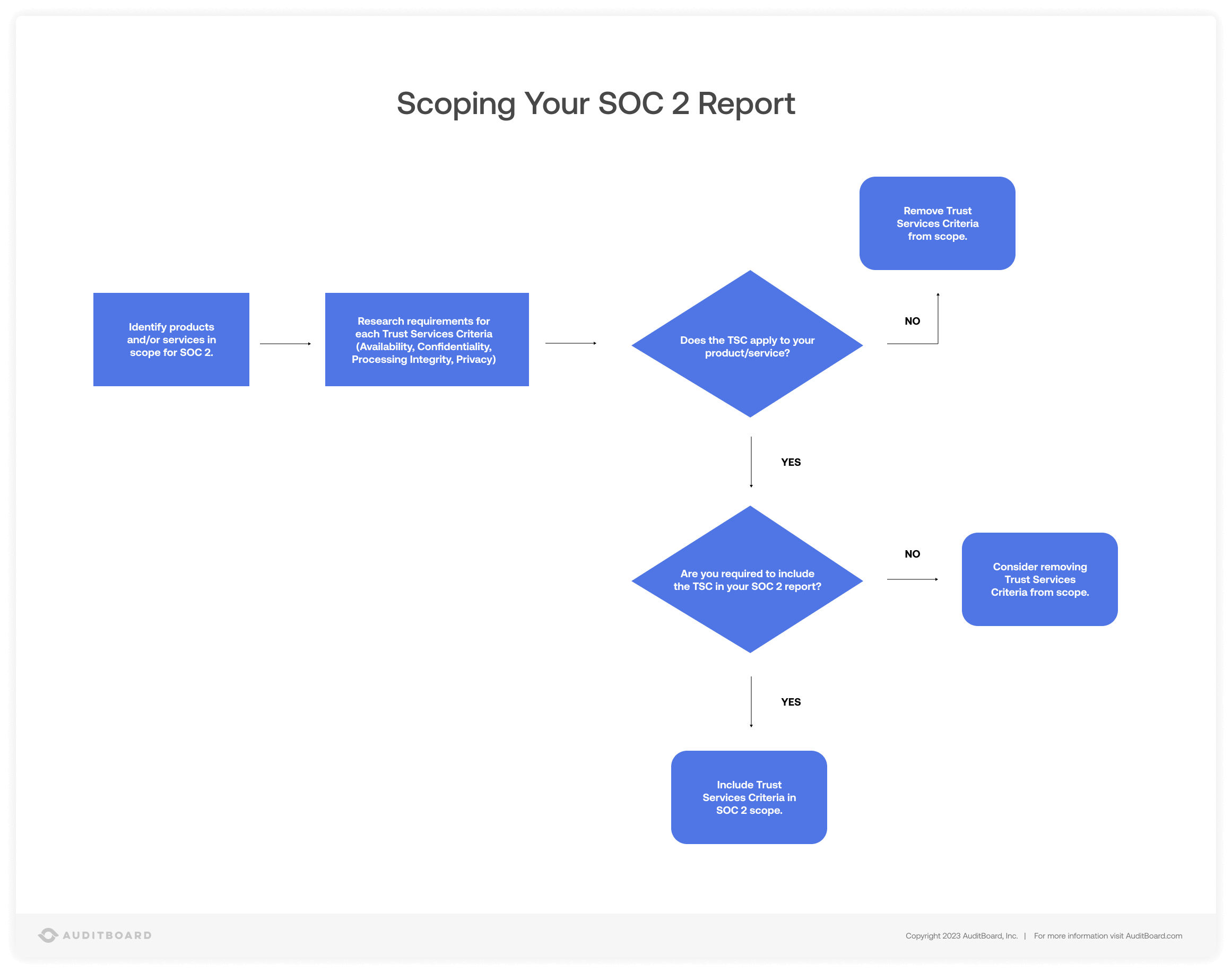
How to execute a SOC 2 program
As with all cybersecurity policies, organizations should continuously monitor key control activities aligning with the Trust Services Criteria. Below, we offer some best practices for executing activities that meet the TSC, which should all be reviewed and updated at least annually.
- Establish an information security program
- Maintain an organizational structure
- Third-party risk assessment/vendor reviews
- Conduct a risk assessment of the in-scope environment
- Mitigate identified risks
- Establish and maintain a compliance evaluation program
- Document and update in-scope control activities
- Conduct security awareness training
SOC 2 requires detailed documentation of all control activities within the audit's scope; you must demonstrate that these controls functioned effectively throughout the entire period covered by the report.
This ongoing effectiveness is assessed during the external audit, and you must provide evidence to support this during the audit process.
How Internxt Drive can help your business get SOC 2 certified
Now you know the requirements and execution process to get SOC 2 certified, here is how Internxt Drive’s cloud storage plans can help you meet the requirements with its secure, encrypted cloud storage for business plans or an object storage subscription.
Internxt complies with ISO 27001 HIPAA, GDPR, and SOC 2, giving your business everything you need to secure company and client data.
Internxt Drive: Security
Internxt Drive can significantly aid businesses in achieving SOC 2 certification by aligning with its stringent security criteria. The platform is fully audited for security, so the company has experience in meeting the highest security standards.
SOC 2 emphasizes protecting systems against unauthorized access, disclosure, and damage, ensuring data availability, integrity, confidentiality, and privacy.
One of Internxt Drive's core features is end-to-end encryption using AES-256 the industry standard for secure confidential and sensitive information. This type of encryption means that files are encrypted directly on the user’s device before they are uploaded.
Since encryption occurs before data leaves the device, it is protected from unauthorized access during transmission and stored on Internxt’s servers. As a result, even Internxt cannot access the contents of the files, ensuring that data remains confidential and secure.
Internxt Drive also focues on data redundancy and backup, which is crucial for maintaining data integrity and availability.
Files are backed up and spread across multiple servers, creating several copies to prevent data loss. This redundancy ensures that if one server fails, the data remains accessible from other servers, thus protecting against potential data loss.
When files are uploaded, Drive breaks files into encrypted segments and distributes them across different servers for maximum security. This method enhances security because even if an attacker gains access to a server, they would only find small, encrypted fragments of the data, not the complete file. This segmentation helps maintain data confidentiality and integrity.
For secure file sharing, file sharing options are available via encrypted links or emails. Users can also set passwords for additional protection, ensuring only authorized individuals can access shared data. This control over file access supports SOC 2’s confidentiality requirements.
Finally, Internxt supports two-factor authentication (2FA), which adds an extra layer of security to user accounts. By requiring a second form of verification in addition to the usual password, 2FA helps prevent unauthorized access and enhances the system's overall security.
Internxt Drive: Availability
Internxt regularly updates its products to ensure continued functionality and optimal performance.
Being an open-source platform, security experts can review the code, ensuring that security measures are current and effective. This transparency allows for timely detection and resolution of potential vulnerabilities, contributing to system reliability.
Internxt Drive's backup systems, which we covered in the security section. also meets the availability criteria. Data redundancy ensures that in the event of a disaster or server failure, users can quickly recover their files from other servers, preventing data loss and minimizing downtime.
These features ensure Internxt Drive's systems remain operational even during unforeseen events, aligning with SOC 2's focus on system availability and disaster recovery preparedness.
Internxt Drive: Processing Integrity
Internxt Drive aligns with SOC 2's processing integrity criteria by encrypting all data throughout its processing lifecycle, maintaining integrity and accuracy. Internxt never stores any data in its decrypted form.
Internxt’s session management supports processing integrity by allowing account managers to monitor remote sessions in real time, ensuring that data is accessed and processed only by authorized users.
By tracking details like client device, OS, IP, and location, it helps ensure that systems are functioning as intended and that unauthorized access, which could compromise data integrity, is promptly detected and addressed.
Internxt Drive: Privacy
Internxt meets SOC 2’s confidentiality and privacy criteria by ensuring that personal information is never collected, used, or shared with third parties, unlike other cloud storage providers like Google Drive, Dropbox, or Microsoft.
It is also a GDPR-compliant company that follows strict European laws related to data handling and protection, guaranteeing that your business information is kept secure.
By maintaining these values for privacy and user data, Internxt guarantees the privacy of your business information, employee information, and files.
Internxt Drive: Points of Focus
Internxt can help stakeholders, auditors, and customers understand how it meets the four criteria discussed earlier through its official documentation, such as the Internxt White Paper. The source code is also publicly available via Internxt's GitHub.
Internxt Business Plans
Internxt offers two plans for businesses to get started with the SOC certification process, and both offer fully private, scalable, and affordable cloud storage for companies or enterprises.
Business plans are available for up to 100 users monthly or annually.
- Standard: €6.99/user/month or €79.99/user/annually
- Pro: €8.00/user/month or €99.99/user/annually
Internxt Object Storage
Internxt object storage offers an affordable, secure way to manage large-scale data, up to 80% more affordable than AWS. It offers a pay-as-you-go pricing model, and you can adapt the storage plans to meet your needs, starting at €7 per TB charged monthly.
SOC 1 vs SOC 2: what are the differences?
As the America Institue of Certified Public Accountants (AICPA) requires, only Certified Public Accountant (CPA) organizations can conduct SOC 2 audits and create and attest corresponding reports. Once the audit is completed, a CPA organization can create two types of reports after performing a SOC 2 assessment.
SOC 1 report
The purpose of SOC 1 reports is to evaluate the effectiveness of controls related to financial reporting and how a service organization’s controls affect its clients' financial statements.
This is relevant for service organizations that influence financial statements, such as payroll processors or payroll outsourcing services and accounting firms.
SOC 2 report
SOC 2 reports evaluate controls related to how well a service organization manages and protects customer data. There are two types:
- Type 1 reviews the design of controls at a specific point in time.
- Type 2 assesses the operational effectiveness of these controls over a period of time, typically 6 to 12 months.
SOC 1 vs SOC 2: key differences
An overview of the SOC 1 vs SOC 2 reports is outlined below.
Scope
- SOC 1: Focuses on financial controls relevant to financial reporting.
- SOC 2: Emphasizes broader data protection and security practices.
Audience
- SOC 1: Designed for clients and stakeholders concerned with financial reporting.
- SOC 2: Targeted at those interested in data security, availability, confidentiality, and privacy.
Criteria
- SOC 1: Based on the Statements on Standards for Attestation Engagements (SSAE) No. 18.
- SOC 2: Uses the Trust Services Criteria established by the AICPA.
Understanding these distinctions helps organizations select the right SOC report based on their needs and client concerns.

Ready for SOC 2 certification?
Gaining SOC 2 compliance is a great step to getting SOC 2 certified and offers significant benefits for organizations by demonstrating their commitment to privacy.
This certification helps build trust and credibility with clients and stakeholders, showcasing that the organization adheres to the best data security practices.
By choosing Internxt as your cloud storage provider, you can meet the requirements for SOC 2, GDPR or HIPAA and demonstrate to stakeholders and clients your business takes every security measure to protect confidential information and sensitive data.

