Remote Access Security Vulnerabilities and How to Prevent Them
In the age of remote working, businesses and freelancers enjoy the freedom of working from anywhere, but this freedom could also come at a cost.
Phishing, hacking, and ransomware are all potential problems businesses and individuals face. To prevent these threats, it's crucial to have awareness of remote access security, the vulnerabilities we face in the age of remote work, and what tools are available to prevent these threats.
This article will explain everything you need to know about remote access security and how Internxt can offer you various services and products to protect the privacy of your data online.
Table of contents
- What is remote access security?
- Remote access security vulnerabilities
- Remote access security strategies
- How Internxt Drive can improve your remote access security
What is remote access security?
Remote access security involves protocols of different tools, apps, and cybersecurity practices to keep connections safe at the office, home, or when working remotely.
Methods such as strong passwords, 2FA, encryption, firewalls, and VPNs are all used to stop unauthorized access to sensitive data. Remote access security also includes monitoring user activity, access limits, and updating software to prevent security flaws such as a zero-day exploit.
The goal of remote access security is to let employees work remotely without exposing themselves or the company to cyberattacks or data breaches.
Remote access security vulnerabilities
Unauthorized access
Accessing systems without permission is a serious threat to companies because it can lead to stolen information, malware, data leaks, or sabotaged operations.
Attacks on remote desk protocols are one of the most common attacks that are achieved by weak passwords, unpatched software, or phishing messages that trick users into granting hackers access.
One example is the 2021 attack on a Florida water treatment plant, where a hacker broke into the system and attempted to raise the water’s sodium hydroxide levels to dangerous levels. Fortunately, the attempt was caught just in time, but it shows the dangers of these kinds of attacks and the need for strong remote access security.
Unauthorized apps
If a worker downloads an unauthorized app without the necessary knowledge, they could download a fake app that could bypass security controls, expose sensitive data, download ransomware, or provide backdoors for hackers to enter the system.
Phishing and social engineering
Phishing and social engineering are common scams where hackers try to manipulate workers via WhatsApp scams or other methods, such as AI phishing.
- In 2024, 42% of organizations experienced phishing or social engineering attacks.
- • Phone-based attacks (vishing) surged by 442% in late 2024, often spoofing IT support or service staff.
Phishing attacks are becoming more advanced and dangerous, with the rise of AI, scammers are now using AI to generate audio and visual deepfakes to trick workers into revealing login details to remotely access sensitive data.
Lack of protocols
A study by the University of Michigan found that a lack of remote access security, i.e., no MFA, VPN, or lack of access controls, opened the network to brute force attacks.
Without documented protocols, it's close to impossible for an organization to monitor, prevent, and stop cyberattacks, as it leaves them vulnerable to cyberattacks and may also lead to compliance fines due to a lack of security to protect customer data.
Misconfigured controls
Even if you have the right controls, if they are misconfigured, there is still a high risk of leaving systems exposed. Incorrect controls are one of the top causes of security breaches due to missing restrictions on remote desktop protocols.
If these controls aren’t set up correctly, hackers can gain access to the network by guessing the credentials or using other methods such as brute force or dictionary attacks.
Insufficient timeout policies
Leaving sessions active even when the worker isn’t actively using the service or account leaves the session open to network hijacking.
Companies should adopt policies where sessions automatically log out after a certain period, such as 10 minutes, to prevent accounts from being hijacked.
Leaving default credentials unchanged
Leaving the default passwords on wifi routers or other devices and applications is another threat to workers and businesses.
The default credentials of many of these devices are published online on dark web blogs or forums, so hackers can use these to hack your wifi, SSH server, or RDP service.
Another security risk is not changing credentials if a worker leaves the company. If the employee leaves, they could maliciously use the credentials by posting them online, or stealing sensitive data or finances after they leave.
Passwords should always be changed for a new device, and then changed at least every three months, or if you are alerted to a security attack on your devices or accounts.

Remote access security strategies
Now we know about the kinds of remote access security risks, here’s how to prevent them.
Log user activity
Logging user activity helps remote access security by creating a detailed record of who accessed what, when, and from where. With it, detecting unusual behavior and tracing the source of incidents becomes much easier. It also helps companies prove compliance with security policies to avoid fines and data breaches.
Typically, you should log:
- Login times
- IP addresses
- Accessed systems
- Actions performed
These features are available with Internxt cloud storage for business, and are one of many features Internxt uses to protect your data from being breached online.
Adopt a zero-trust approach
Zero trust policies help prevent system attacks due to account inactivity and other means. The policy is based on verifying the user at all times and ensuring that they only have access to the necessary systems.
Zero trust reduces the risk of lateral movement, so if a hacker does gain access to one area, the attack can be quarantined and reduced so other areas aren’t affected. It is useful in stopping internal threats and is especially important for remote work, where users are connecting from many locations and devices.
Backup data
Backing up your data ensures you have multiple copies of it available in different locations to protect against ransomware and data loss or corruption.
Backups are especially important for remote access security because remote systems are more exposed to ransomware and unauthorized access. Having different types of backups, ideally using different backup methods and locations, is a crucial step to protect corporate data.
Encrypt the data you send online
Encrypting sensitive files when you send files online will prevent external attackers from intercepting information and viewing sensitive or confidential files.
When combined with password protection, link expiry, and access controls, sharing files online using encrypted services will prevent data leaks and unauthorized access.
Services such as Internxt Send or Internxt’s advanced folder sharing options are both solid and secure tools for remote workers.
Use strong passwords or passphrases
Weak passwords and hygiene are one of the first vulnerabilities hackers will target, so it's crucial to protect all accounts, devices, and other applications with a strong password or passphrase. You should store these using a reputable and trusted password manager, and limit access to them to essential workers only.
Use Internxt's Password Generator and Password Checker to generate powerful passwords and passphrases, which you can check to guarantee you have a strong password to protect your accounts and devices.
IP whitelisting
IP whitelisting is another essential remote access security process to block external threats. Whitelisting means you only allow specific, trusted IP addresses can access a system or network.
It’s often used with other authentication methods, as remote workers will change their locations often, but it is still a valuable protocol to be aware of.
Use a VPN and MFA
VPNs are not only useful for accessing restricted content from certain countries, but they also encrypt your network to prevent hackers from intercepting your connection. An encrypted VPN, like the one offered at Internxt, secures your connection, hides your IP, and keeps your sessions private.
Another tool is MFA, so you can combine these methods with a strong password as an additional security measure. MFA can be FaceID, fingerprint, a code or link, or other methods that prevent hackers from breaching your account, even if they gain access to your password.
Update and patch your software
Keeping software up to date is crucial because attackers often exploit known weaknesses in outdated systems to gain unauthorized access. For example, if a remote desktop tool or VPN has a security flaw that hasn’t been patched, hackers can use it to break in.
Whenever your system notifies you of an update, make sure to activate it as soon as possible to prevent cybercriminals from taking advantage of outdated software.
Employee training
A large part of data breaches is due to human error and a lack of awareness.
Training remote workers about cybersecurity basics and regularly updating employees about the best security practices helps prevent mistakes like falling for phishing scams, using weak passwords, or sharing access improperly.
Be aware of compliance laws
Compliance laws help protect corporate and customer data, and could save businesses millions by preventing data breaches.
Knowing which compliance laws to follow will depend on your industry, but the most common ones are GDPR, CCPA, and HIPAA. More information about the different types of compliance can be found in the business section of our blog.
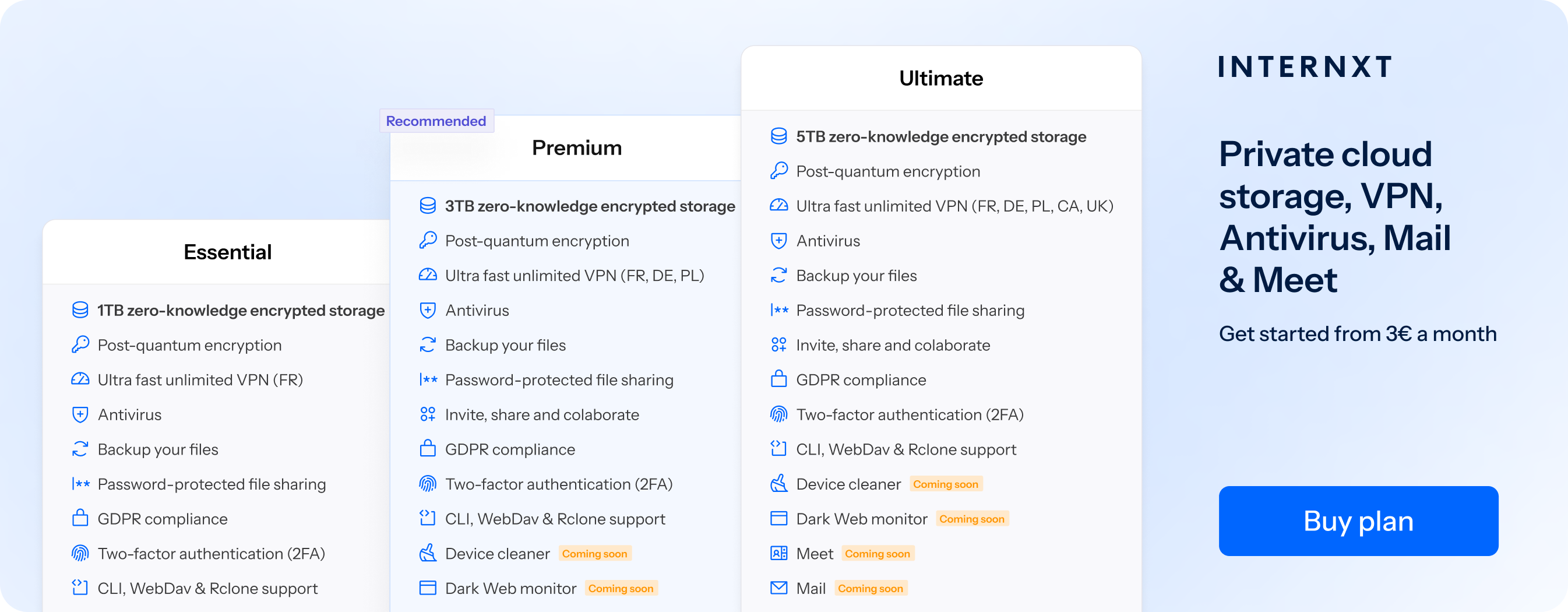
How Internxt Drive can improve your remote access security
Access logs
Internxt Business plans come with access logs to track who has signed in, uploaded, or modified files. With these advanced security controls, you can easily monitor your account activity to prevent unauthorized access.
Post-quantum encrypted cloud storage
Internxt is the first cloud storage to use post-quantum encryption.
This advanced cryptography method protects your data from the future threat of quantum computers, which could potentially break current protocols due to their ability to solve the complex mathematical problems encryption relies on.
With our post-quantum encryption, Internxt ensures your data is protected against these future threats. This encryption, combined with our zero-knowledge policy, offers you the best privacy and security for your data.
Backups
Internxt plans also include encrypted backups to protect your business from data loss, corruption, or ransomware.
You can schedule your backups so you always have the most recent copy of your files available. We store your backups in multiple locations to increase redundancy, so you can always recover your files no matter what happens.
VPN & Antivirus
Business plans also come with a VPN, an encrypted, ultra-fast, and unlimited service to encrypt your connection and hide your IP address for up to 5 locations.
Internxt Antivirus is also included with Internxt paid plans to scan and remove malware from your device for increased remote access security.
Upcoming features: Device Cleaner, Dark Web Monitor, Meet, and Mail
Later this year, Internxt will release a Device Cleaner to remove junk files to optimize device performance, and a Dark Web Monitor to notify you if your email has leaked in a data breach.
Ultimate and Pro plans will also include an encrypted email and video conferencing platform, offering you an extensive range of products to protect your privacy online.
GDPR compliance
Internxt is a GDPR compliant cloud storage company based in Europe, so it complies with strict European laws to ensure your data is handled and respected.
Get started with Internxt with a free account, or join our join our paid plans, which start from €3/month for annual plans, or €6.99/month/user for business plans.

