iPhone Security: How to Remove A Hacker From My iPhone

We have all become pretty familiar with our smartphones due to the amount of time we spend on them. According to recent data, the average user spends 3 hours and 15 minutes on their phones every day.
As a result, the chance of you noticing something is not quite right with your phone is quite high. However, knowing the cause of the problem and how to fix it can be slightly more difficult.
Is your iPhone behaving strangely due to outdated software, age, or hardware problem? Or, perhaps, has it been compromised by a hacker? If it’s the latter, we're here to help you identify the signs of a hacked iPhone and answer the question of how to remove a hacker from your iPhone.
We will offer advice regarding stolen device protection for iPhone and how to use this setting to secure your devices. The new iPhone iOS 17 update has released new security measures that will also keep your iPhone safe in case an iPhone hacker steals it or a street criminal accesses your phone to steal your finances, erase the data from your phone, and sell it.
Table of Contents
- What are the signs an iPhone hacker has access to your iPhone?
- How to remove a hacker from my iPhone
- How Stolen Device Protection for iPhone can help your mobile security
- Protecting yourself from an iPhone hacker or thief
What are the signs an iPhone hacker has access to your iPhone?
If you notice any suspicious activity on your phone or it's not performing as usual, an iPhone hacker may have breached your Apple ID and accessed your account.
Higher iPhone temperature and battery drainage
If your iPhone feels unusually warm even when you're not using it heavily, it could be a sign that malware or harmful apps are running in the background. These apps can drain your battery life much quicker than usual.
Your camera or microphone light is on
Another sign an iPhone hacker has compromised your device is accessing your camera or microphone in the background. The orange light is an app using your microphone, and the green light is for the video.
If these lights are on when you're not actively using those features, it could indicate an app is accessing them without your knowledge.
Unauthorized purchases or apps
Have you noticed strange charges on your Apple ID bill or unfamiliar apps on your home screen? Hackers might use your account to make unauthorized purchases or install apps to steal your data.
High data usage
In addition to draining your battery, unauthorized apps can drain your monthly data. A spike in this data that doesn’t coincide with your typical data usage can indicate malware sending or receiving information from the background.
Locked out of Apple ID
This is the most obvious sign an iPhone hacker has accessed your device. If you can't access your Apple ID due to incorrect login attempts you didn't make, your iPhone is likely compromised.
Other signs your iPhone may be hacked
Aside from these, other signs may include:
- Unusual Pop-Ups and Ads: A sudden influx of intrusive pop-ups or ads you wouldn't usually see can indicate adware or malicious software.
- Slow Performance: Is your iPhone feeling sluggish and unresponsive? While this could have other causes, it's worth considering if it coincides with other suspicious behavior.
- Strange Text Messages or Emails: Phishing attempts often come through texts or emails disguised as legitimate sources. Be wary of messages urging you to click on suspicious links or download attachments.
If you notice any of these signs or anything unusual about your iPhone, you can take steps to remove an iPhone hacker from your phone.

How to remove a hacker from my iPhone
Securing your Apple ID is the first step in removing an iPhone hacker from your iPhone and protecting your device.
Manage your Apple ID
Your Apple ID is the most powerful defense to protect your account, so follow these steps to change it and add additional security methods to ensure you have the best security to protect your account.
- Change your Apple ID password
- If your Apple ID password has been changed by someone else, reset your password.
- Go to appleid.apple.com to update any of personal or security information that isn't correct or that you don't recognize.
- Check with your email address provider to make sure that you control every email address associated with your Apple ID. If you don't control an email address, work with your email provider to regain control or use a different email address.
If you can't reset your Apple ID password or sign in to appleid.apple.com, go to iforgot.apple.com to start account recovery and regain access.
After you request account recovery, you get a confirmation email within 72 hours with a date and time when you can expect to regain access.
Find out who is signed into your device
You can check your settings to make sure only trustworthy accounts are signed in to your Apple ID. Here’s how you can find out:
- Open the Settings app on your iPhone or other Apple devices.
- You should see your name. Tap your name and verify the email address associated with your Apple ID.
- On each device, check the settings for services that you're signed in to with your Apple ID (including FaceTime, Messages, the iTunes Store and the App Store, Internet Accounts, Mail, and Calendar).
How to secure your Apple ID
Aside from creating a strong password, you should also add more layers of security to your device and Apple cloud storage, from an iPhone hacker or if your iPhone is stolen.
- All accounts should have Two-Factor Authentication, and your Apple device is no different.
- Never share your Apple ID, passcode, or password with anyone. Be wary of any emails or messages asking for your details.
Set up a recovery contact
You can trust a recovery contact to help you regain access to your account; it can make regaining access and changing your Apple ID easier. A recovery contact should be someone you trust, such as a family member or close friend.
You can set up a recovery contact on iOS 15 or later. Here’s how:
- Go to Settings, then tap your name.
- Tap Sign-In & Security, then tap Account Recovery.
- Tap Add Recovery Contact, then tap again and authenticate with Face ID or Touch ID.
- If you're in a Family Sharing group, group members are recommended. Or you can tap Choose Someone Else to choose one of your contacts.
- If you select a family member, they're added automatically. If you select a contact, they need to accept the request. You also send them a message to let them know you'd like to add them as your recovery contact.
- After they accept your request, you see a message that they have been added as your account recovery contact.
How Stolen Device Protection for iPhone can help your mobile security
Hackers are not the only threat to your iPhone. Thieves often target people using social engineering techniques to “borrow” and gain access to your phone. Some cybercriminals target college bars and ask if they can borrow your phone. In the process, they memorize your passcode.
How thieves and iPhone hackers access your phone
Before the recent update of stolen device protection from the iOS 17 update, iPhones had a huge security vulnerability that could cause people to completely lose access to their phones.
A famous example of this is iPhone hacker and thief Aaron Johnson, who was arrested and charged with racketeering and sentenced to over 90 months in prison. Johnson would target college students in bars and gain their trust under false pretenses.
He would access students’ phones by offering to put his number on them. He would watch them enter their passcode and memorize it; if he had the phone, he would ask them to give him the passcode to unlock it and enter his number.
Within 5 - 10 seconds, Johnson would go to settings, iCloud, enter the passcode, change the password, and delete the Find My iPhone feature.

From there, he had complete control of the person’s phone and would remove their face from Face ID and change it to his own. Now, Johnson would go to their mobile banking apps, PayPal, Venmo, or crypto apps, and take everything.
He would then check their notes for passwords to other apps or social security numbers. Before erasing all the data from the iPhone, he would go shopping, pay for everything using Apple ID with his Face ID, and then sell the phone.
Fortunately, the new iPhone update includes stolen device protection, which can prevent this from happening.
How to enable stolen device protection on iPhone
The Stolen Device Protection for iPhone protects your accounts and personal information in case your iPhone is ever stolen. It enables additional security requirements when your phone is away from familiar locations your phone tracks, like your home or workplace.
Here's how you turn on this security feature:
Before you turn on Stolen Device Protection, you need to have 2FA, a device passcode, Face ID or Touch ID, and Significant Locations activated.
- Go to Settings, then tap Face ID & Passcode.
- Enter your device passcode.
- Tap Stolen Device Protection, then turn Stolen Device Protection on.
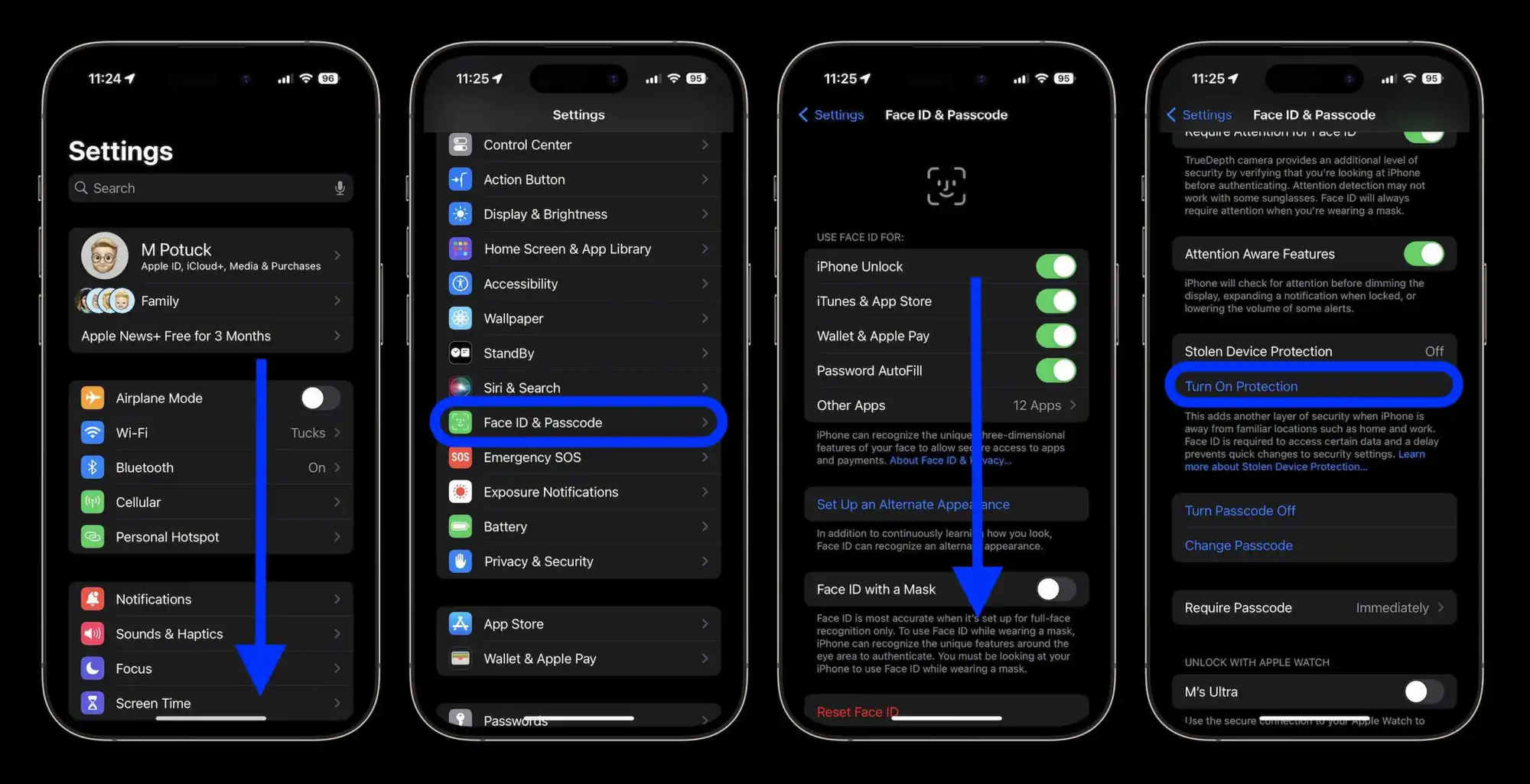
You can set up this protection regardless of location under Stolen Device Protection > Require Security Delay > Always.
This sets up a delay that will always be required to change security settings.
If you sell, trade, or give away your iPhone, you should turn off this setting and factory reset it.
Stolen device protection on your iPhone prevents someone who has stolen your device or passcode from making changes to your account or device, giving them access to your finances and erasing all the data on your iPhone.
- Face ID or Touch ID biometric authentication: accessing stored passwords or credit cards requires a single biometric authentication with Face ID or Touch ID — so that only you can access these features.
- Security Delay: Some security actions, such as changing your Apple ID password, also require you to wait an hour and then perform a second Face ID or Touch ID authentication.
These steps are not required if your phone is in a familiar location.
How the Stolen Device Protection can prevent an iPhone hacker or thief
When your phone is away from usual locations, your Face ID or Touch ID is required before these actions can be completed:
- Use passwords or passkeys saved in Keychain
- Use payment methods saved in Safari (autofill)
- Turn off Lost Mode
- Erase all content and settings
- Apply for a new Apple Card
- View your Apple Card or Apple Cash virtual card number
- Take certain Apple Cash and Savings actions in Wallet (for example, Apple Cash or Savings transfers)
- Use your iPhone to set up a new device (for example, Quick Start)
Protecting yourself from an iPhone hacker or thief
With the new iOS 17 update, Apple is helping its users prevent financial losses or identity theft. If you don’t have this update, updating the software for all your Apple devices is crucial, so you don’t have to worry about losing your phone, money, and more.
Regular updates will also prevent an iPhone hacker from accessing your Apple ID or installing malware or harmful software.
Remember to monitor your Apple accounts' activity regularly and enable all the security features required to defend them—the more, the better. Software updates are crucial for security, so stay updated and install them as soon as they are available.

