Cryptography Terms Explained: Definitions And Concepts Made Simple

Interested in learning more about cryptography but don’t know where to start? We break down the common cryptography terms in a simple and clear way, to help you understand how companies encrypt your data in a safe and secure way.
From there, you can dive deeper into the world of cryptography and learn more about this important and fascinating concept.
Table of contents
- Core concepts of cryptography
- Cryptography terms for types of encryption
- Key management and exchange
- Cryptography terms for data integrity and authentication
- Conclusion
Core concepts of cryptography
Let’s start with the fundamental ideas and cryptography terms that underlie all cryptographic systems.
Cryptography
Cryptography hides information in messages, emails, or other forms of communication, such as sharing files online, so only the intended recipients can read the information. It turns the message into a scrambled, unreadable code, so no hackers can view the information. Cryptography has been around for tho
Cryptography has been around for thousands of years, starting with the Egyptians and Greeks sending coded messages known as the Caesar cipher, shown below.
As history and technology developed, cryptography became an essential part of World War II with the Enigma machine, and now uses advanced computers and mathematics to protect files, passwords, and sensitive data.
Plaintext
Plaintext is what you are reading now; it is text or information that isn’t encrypted. This is why cryptography is essential, because if sensitive information is sent via the internet, anybody can read your emails, passwords, and everything else.
Ciphertext
Ciphertext is text that has been encrypted from its plaintext form to a scrambled, unreadable form using encryption.
For example:
- Plaintext: Please join the meeting at 11:00
- Ciphertext: w9QeZ71RybwQkA1HeJ1x0WyWhu4RZJ8Pz+jBoEw5mNk=
Without the correct encryption key, no one can read or change the text back into the original message.
Cipher
In cryptography terms, a cipher is a method or set of rules used to turn plain text into secret code (ciphertext) and back again. A cipher decides how the information is scrambled during encryption and how it's unscrambled during decryption.
Key
A key works with a cipher to encrypt and decrypt data. The key is sometimes held by cloud providers like Google, or is managed on your device, like Internxt, but more on that later.
Without the correct key, the information can’t be viewed, decrypted, keeping your data and information secure.
Cryptography terms for types of encryption
These are some common cryptography terms you may have seen regarding techniques used to encrypt and decrypt data.
Symmetric key encryption
Symmetric key encryption is the simplest kind of encryption involving one key to cipher and decipher information, as shown by the diagram below.
The sender and the receiver must have the same secret key to read the message. Platforms like WhatsApp use symmetric key encryption to encrypt messages on the sender’s device, which shares the secret key with the recipient so the device can decrypt it and the recipient can read it.
Asymmetric key encryption
Asymmetric key encryption differs from symmetric key encryption because it uses two different keys: public and private, whereas symmetric only uses one secret key.
Asymmetric encryption uses one public key to encrypt a message and one private key to decrypt it. The receiver shares the public key with the sender, who uses it to lock the message. Only the receiver, with the private key, can unlock and read the message.
Online and mobile banking uses this kind of encryption, as the browser encrypts critical information with the bank’s public key, but the bank’s server has a private key.
Block Cipher
A block cipher breaks down and encrypts data in blocks using a cryptographic key and algorithm. Block ciphers encrypt using a symmetric key and algorithms to encrypt data in fixed-size blocks of either 64 or 128 bits to provide more security and efficiency.
Stream cipher
A stream cipher encrypts plaintext one bit or byte at a time, instead of in fixed-size blocks. This continuous flow of data is called a stream. A key stream, generated from a secret key, is used to encrypt the data. The same key stream is needed to decrypt it back into the original message.
Stream ciphers are used for data that’s sent in a continuous flow, such as voice calls, video streams, or live chats.
AES (Advanced Encryption Standard)
Advanced Encryption Standard is likely to be one of the cryptography terms you have heard the most, as it is highly recommended to everyone looking to encrypt and secure data.
AES is a symmetric encryption algorithm that uses a block cipher to encrypt data in fixed-sized blocks. It uses various key lengths, 128, 192, or 256, to encrypt data in blocks and protect against unauthorized data access.
RSA
RSA encryption is a type of asymmetric encryption that uses public and private keys. The algorithm is named after Ron Rivest, Adi Shamir, and Leonard Adleman, who published it in 1977.
RSA isn’t as common as other types of encryption methods because it uses larger key sizes and is therefore slow. It’s also becoming less common due to newer, more secure methods such as the next additions. Still, it’s one of the cryptography terms you should know about.

In 2020, research showed vulnerabilities in RSE public keys. After analyzing more than 75 million active RSA keys from the internet, they discovered that 1 in every 172 certificates using RSA is vulnerable to factoring attacks.
A factoring attack is where someone breaks RSA encryption by figuring out the two prime numbers used to create the key.
Zero-knowledge encryption
With encryption keys, they can be managed by two parties: the cloud storage provider or you. The latter is known as zero-knowledge encryption, and by managing the encryption keys on your device, it's a much more private encryption method than services that manage the encryption keys.
With Google Drive or Dropbox, for example, they manage the encryption on their servers, meaning they could potentially decrypt your files and view their contents, or give access to your files if required by law enforcement.
This is why Internxt Drive uses zero-knowledge encryption for its cloud service and other products, giving you total privacy of your files, so nobody but you can view their contents.
Elliptic Curve Cryptography (ECC)
Due to advances in computing power and technology, these new cryptography terms may get a bit difficult to understand, but we’ll do our best to explain.
Elliptic curve cryptography is a public key algorithm to perform the most critical security functions, such as encryption, authentication, and digital signatures.
Rather than traditional encryption methods that rely on factoring large numbers, ECC uses the mathematical principles of elliptic curves over finite fields, so it’s considered more secure than RSA.
ECC is becoming more widely used due to its high security, lower computing power, and faster speeds.
The encryption process works by starting at one point on the curve and repeatedly adding it to itself a specific number of times. The point you end up at becomes your key.
This is useful because it's nearly impossible for computers to figure out how many steps the encryption process took to give you your key, ensuring your data remains secure and private.
Post-Quantum Cryptography
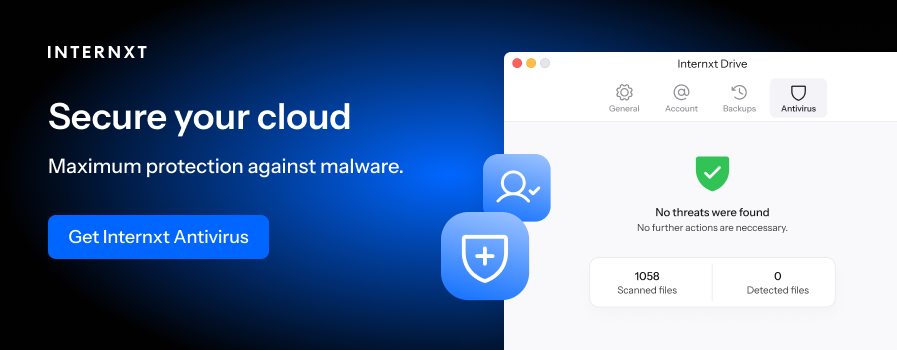
Finally, we have post-quantum cryptography (PQC), which is the encryption Internxt uses, making it the first cloud storage to have and use post-quantum and zero-knowledge encryption.
PQC is an encryption method designed to protect against the threat of quantum computers, which have the potential to break the current encryption standards.
Post-quantum encryption has the potential to solve mathematical problems that classical computers cannot, such as factoring large numbers and computing discrete logarithms using algorithms like Shor’s algorithm.
PQE aims to protect against this threat with lattice-based cryptography. It uses structures called lattices, which are like grids of points in many dimensions with an infinite number of possible vectors, making it close to impossible for quantum computers to solve.
Internxt uses Kyber-512 post-quantum encryption, selected by the NIST to protect against the future threats of quantum computers.
Key management and exchange
Cryptography terms you will see about how cryptographic keys are generated, exchanged, and verified.
Key exchange
Key exchange is where you and someone else create a shared secret key to securely communicate, a key cryptography term, as key exchange is essential for encrypting and decrypting messages.
Diffie-Hellman key exchange
Diffie-Hellman key exchange helps people create a secure way to create and share cryptographic keys over the internet without anyone intercepting the conversation. It’s used in secure protocols such as Transport Layer Security (TLS) and others.
Two people each pick a secret number and use math involving raising numbers to a power to generate partial keys, which they then share. Using the other person’s shared value and their own secret number, both calculate the same shared key to encrypt and decrypt data.
Public Key Infrastructure (PKI)
PKI helps verify identities and securely exchange information online by proving a public key belongs to a specific person or organization.
So if you visit a website, your browser checks its digital certificate to confirm its identity by a Certificate Authority. Once verified, your browser encrypts the information you send, such as your password or credit card details.
Without it, hackers could easily steal your information.
Certificate Authority (CA)
A Certificate Authority is a company or organization that verifies the identity of people, websites, or companies and then issues digital certificates. Popular companies that provide this certificate are:
- DigiCert
- Let’s Encrypt
- GlobalSign
These certificates link a public key to the verified owner, helping users trust that they are communicating with the right party securely.
Digital Certificate
This is an electronic document that proves the ownership of a public key and includes information about the owner’s identity and the public key, which is verified and signed by one of the trusted certificate authorities mentioned above.
Cryptography terms for data integrity and authentication
Checking the integrity and authentication of data ensures it hasn't been altered.
Digital Signature
A digital signature is the process of verifying the authenticity and integrity of messages and signatures online using cryptography techniques.
It generates a unique signature of the content and the sender’s private key, which can be verified with the public key to ensure the message is from the original sender and hasn’t been tampered with.
Hashing
Hashing uses mathematics to convert data into a fixed-size string of characters, like this:
f2b127f3e5d78615e4e0ab5de1b1f2059b357327f2536db3baf7d2f3e48e8c3e
The process is irreversible, so the original data cannot be retrieved from the hash so changing one input will create a completely different hash.
Hashing is a process that happens when you create a password on a website. As websites don’t store your passwords, instead, they store the hash. So when you log in, your password is hashed and compared to the stored hash. If they match, you can access your account.
Hashing is crucial to protect against data breaches, as the hashed data won’t leak your password.
Salt
Now we know what hashing is, imagine if two people have the same passwords, does this mean the hash is the same? No.
Salt is a process that prevents this by adding random data to a password before hashing it, making each password unique and secure.
Nonce (number used only once)
A nonce is a random and unique number used when you log into a website or make a payment. This prevents replay attacks, where a hacker captures a request and sends it again to try and steal money or log in to an account.
Initialization Vector (IV)
An IV is another random value used in encryption to give two different results to data that needs encrypting more than once. If you upload or share photos twice using the same encryption key, the IV adds randomness so the encrypted versions look different.
This stops hackers from potentially noticing patterns and guessing what the original message was.
Perfect Forward Secrecy
PFS is a security feature that makes a new and temporary encryption key for each session between two people.

If you visit a website, for example, PFS ensures that if someone records your data and steals the server key, they still can’t read your messages.
Zero-Knowledge proof
Zero-knowledge proofs are cryptographic algorithms that prove you have the information needed, like your password, without revealing your password.
When you need to prove you have the correct password to access your account, the server sends you a random number, and your password is used to calculate the correct response. If your password is correct, the server checks and authenticates the answer, but without seeing the password.
Conclusion
So there you have it, the most common cryptography terms explained so you know how companies protect your data from hackers, cyberattacks, and data breaches.
For the best and most advanced cryptography to protect your data, you can get post-quantum encrypted cloud storage, VPN, Meet, Mail, and more with Internxt. Join Internxt by choosing any of our lifetime or annual plans from just €3/month to make the switch to privacy and move away from Big Tech.

