What Is Clone Phishing And How Can You Prevent It?
Clone phishing is another scam that threatens our online security and data. Throughout this article, we will analyze what clone phishing is with real-world examples. In doing so, you can help identify this kind of scam and keep your personal and business information safe.
Table of contents
- Account verification
- AI voice clone phishing
- Invoice or payment requests
- Software updates or security alerts
- Two-factor authentication
- Antivirus software
- Secure file sharing
- Use a VPN
- Other tools to prevent clone phishing
- What is an example of a clone phishing email?
- How do I know if my email has been cloned?
- What do you do if you receive a clone phishing email?
What is clone phishing?
Like your traditional phishing emails, scammers send clone phishing emails to trick you into revealing your sensitive information, typically passwords or credit card details. If they gain access, they use this information to access your accounts for identity theft or fraud.
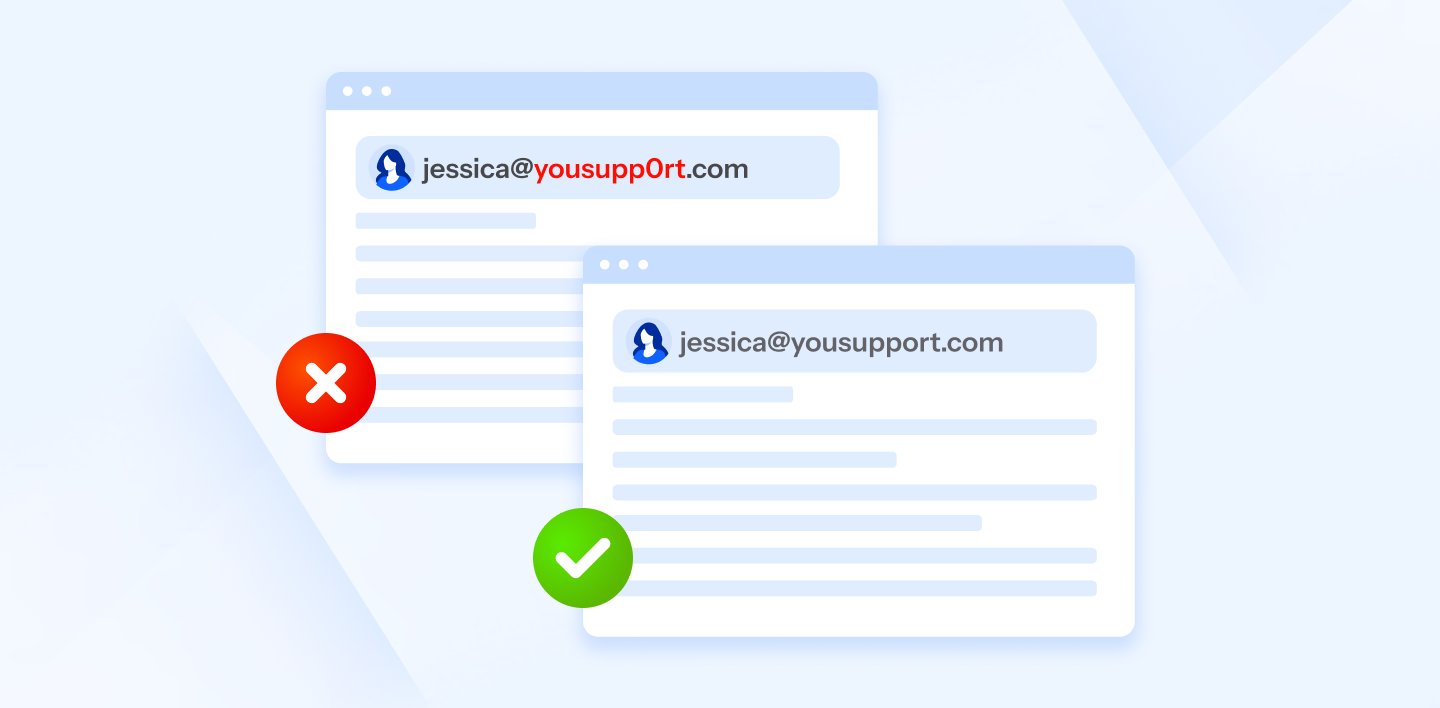
Clone phishing is slightly different in that it takes an original message from a trusted sender and creates an identical copy of the original. The email will copy the email from the known sender, use the same language, branding, and formatting, making it extremely hard to identify as phishing.
Once cloned, the malicious actor will make one small change, typically a malicious link, that directs you to a spoof website designed to steal your personal information.
How does clone phishing work?
First, an attacker will obtain a genuine email their target has received before, such as a password reset email or invoice. This is done by monitoring a victim’s previous communications, which may have happened in a prior data breach, or stealing email templates online.
Once created, they will send the email with the malicious content, justifying the resend with an excuse to ease your doubts.
To be more successful, clone phishing may monitor your email habits before sending you the email to increase their chances of gaining access to your information or install malware on your device.
For example, if you receive multiple emails from PayPal, Amazon, etc., you are more likely to suspect phishing from these companies because they're trusted companies, and you receive similar emails from them all the time.
As a result, it’s more likely you will click on the link without thinking too much about it. To avoid this, always hover over and verify the link beforehand to avoid falling into the trap of clone phishing.

Different kinds of clone phishing
The following are some common examples of clone phishing.
Account verification
Companies will implement security measures to verify your account and guarantee it is you who is trying to log in. While this is essential to protect our accounts, cyberattackers will use it to their advantage.
A scammer will clone an account verification from a bank, social media, or other platform with a link to a fraudulent website to steal your login credentials.
AI voice clone phishing
AI scams are another prevalent issue in the community, as all it takes is for a cybercriminal to take a few seconds of audio from social media to create this kind of clone phishing scam.
Even from such a small sample, AI can use this audio to replicate a voice, create deceptive messages, or have real-time conversations. From there, voice clone phishing may target family members, friends, or colleagues to convince them to transfer large sums of money.
Invoice or payment requests
Fraudulent invoices or payment requests, often associated with Business Email Compromise (BEC) schemes, are sophisticated scams where attackers impersonate trusted vendors or partners.
They gain access to a company’s email communication, either from malware or a data breach, and use this communication to create clone emails of fake invoices to request payments to accounts the scammer controls.
Software updates or security alerts
Updating your software is essential to keeping your accounts protected, as it closes security vulnerabilities hackers can use to gain unauthorized access, spread malware, or other forms of cyberattacks.
As a result, cybercriminals may use clone phishing techniques to exploit this urgency for software updates in their email. Once they send the email, it contains an urgent message notifying the recipient of some sort of software vulnerability that needs fixing immediately.
Instead, the link or download will steal the recipient’s information, or download malware to the device.
Real world examples of clone phishing
To emphasize the growing threats and concerns regarding clone phishing, here are some well-known examples over the past few years.
Android (2024)
A malware strain named NGate targeted Android users by cloning banking applications, disguising them as legitimate app updates to install malicious software that harvested users' banking credentials.
As a result of the attack, the criminals managed to clone bank cards, allowing them to make unauthorized online purchases and cash withdrawals.

Reddit (2023)
In February 2023, Reddit experienced a ransomware attack following a sophisticated phishing email that targeted its employees. The attackers, identified as the ransomware group BlackCat, stole 80GB of data and demanded a $4.5 million ransom for its return.
AI voice cloning scam targets Italian executives (2025)
In February 2025, scammers used AI voice cloning to impersonate Italy’s Defense Minister, Guido Crosetto.
The scammers targeted business leaders like Giorgio Armani and Patrizio Bertelli and falsely claimed Italian journalists were kidnapped, requesting urgent ransom payments for their safe return.
One of the targets fell for the scam, and transferred €1m to a Hong Kong account, believing the Bank of Italy would reimburse them.
Clone phishing vs other phishing
Clone phishing differs from other kinds of phishing, such as spear phishing, as it copies an existing email and sends it to multiple targets to increase the success rate.
Spear phishing, on the other hand, is a more personalized approach, as it focuses on a specific individual. Spear phishing emails are usually sent to a company's high-level executives to access confidential information.
As a result, spear phishing relies more on social engineering techniques, research, and meticulous planning to trick an employee into handing over access to personal information.
Clone phishing, while equally as dangerous, is more straightforward and relies on targeting hundreds of thousands in the hope that someone will fall for the scam.
How to recognise clone phishing
Recognizing clone phishing can be done by following most steps from our other article, How to Identify and Stop a Phishing Attack, but to summarize, the methods include:
- Check for unusual addresses or domain names
- Don’t click on links without checking them first
- Check for urgent language, spelling, or grammar mistakes
- Verify and authenticate with the company if you’re not sure
Compare emails
Clone phishing can also be further verified by comparing the suspected email to the genuine email to check for further anomalies. If you have received the email out of context, this could also be a sign of clone phishing.
Verify and check
You can also check and use some tools to help identify clone phishing, which are:
- Check the email for misspellings, extra characters, letters, or unfamiliar domain names.
- Verify the domain name using lookup or domain verification tools.
- Avoid entering personal information like login details, card details, or anything else via email without first verifying the source.
- Check your email settings to make sure your spam filters are properly set, and use antivirus software and email authentication protocols for additional security.
- Before clicking on a link, hover over it to verify the URL matches the expected destination.
How to protect yourself and employees from clone phishing
Businesses and individuals can prevent clone phishing with the following tools, but it's important to stay updated on cybersecurity practices, such as remote access security, and common attacks for future online protection.
Two-factor authentication
Two-factor authentication will verify that you are trying to access your accounts, so if somebody is trying to access your accounts without permission, you will be alerted on your device and can change your password immediately.
Combine 2FA with a strong password for maximum account security, without these, your risk of being exposed to clone phishing, and other cyberattacks, is significantly higher.

Antivirus software
If you accidentally download a malicious file from a clone phishing email, antivirus can help you delete malicious files from your device, keeping it free from ransomware, viruses, and prevent hackers from accessing your files and sensitive data.
While there are many antivirus options to choose from, Internxt Antivirus is an advanced antivirus software system built into the Internxt Drive app. With it, you get private cloud storage and an antivirus to keep your files clean and your device free from malware.
Secure file sharing
Protecting files with a password keeps sensitive information safe, prevents unauthorized access, and as a result, prevents cybercriminals from cloning documents to use in their phishing attempts.
File sharing options include WeTransfer but for a free, unlimited file sharing service with end-to-end encryption, choose Internxt Send to share large files for free, or Internxt Drive for advanced sharing features.
Use a VPN
A VPN can improve online safety by encrypting your connection over public Wi-FI, preventing threat actors from intercepting your network, stealing your information, and accessing and cloning your emails.
Internxt Drive also offers a VPN with its cloud storage plans, allowing you to surf the web privately and access up to five different locations. With it, you can hide your IP addresss, encrypt your connection, and increase your online security.
Other tools to prevent clone phishing
Here are some free tools from Internxt that will help you prevent clone phishing and increase your online security so you don’t have to worry about hackers or big tech companies stealing your data.
- Free password generator: create strong passwords in an instant.
- Free password checker: check the strength of your password to ensure you have the best account security.
- Temporary email: prevent phishing with a temporary email to keep your personal email private.
- Dark web monitor: check if your email has leaked online.
Clone phishing FAQ
What is an example of a clone phishing email?
A clone phishing email may look something like this and includes the branding and formatting of the company.
Subject: [Action Required] Update Your Account Information
From: support@yourbank.com
To: your.email@example.com
Dear Valued Customer,
We noticed unusual activity on your account during a recent login attempt. To ensure your account's security, please verify your information by clicking the link below:
Verify Account Information
If you do not verify your information within 24 hours, your account may be temporarily suspended.
Thank you for your prompt attention to this matter.
Best regards,
YourBank Security Team
How do I know if my email has been cloned?
If your employees, friends, or family ask you about emails you didn’t send, you receive emails that your messages failed to deliver, your sent folder has emails you know you didn’t send, or you receive numerous phishing emails.
What do you do if you receive a clone phishing email?
Verify the sender and check for inconsistencies in the sender’s address. Don’t click any links unless you verify them by hovering over them first. If you’re unsure, verifying with the company that they sent you the email before you click on any links is best.

