The Benefits & Features of SIEM Compliance to Build a Secure Business

Factors such as scalability, budget, and security must be considered for businesses considering their cloud storage and data management needs. Still, one of the most crucial factors that must be accounted for is what compliance standards must be met.
Compliance with GDPR, HIPPA, SIEM, NIS2, or other bodies ensures the organization adheres to legal, regulatory, and industry standards that are met to protect sensitive data.
On a broader scale, compliance protects businesses from data breaches, avoids fines or legal penalties, simplifies auditing, and helps build a strong reputation and customer trust.
SIEM compliance helps businesses meet regulatory requirements through centralized log management, real-time monitoring, and automated reporting. It also improves data security, simplifies audits, reduces the risk of penalties, and improves incident response and data recovery times.
Throughout this article, we will cover all SIEM compliance requirements, components of SIEM, its role in regulatory adherence, use cases, and how Internxt can help your company adhere to compliance regulations.
Table of contents
- What is SIEM compliance?
- Why companies need SIEM compliance
- SIEM compliance requirements
- SIEM use cases
- How Internxt helps with account monitoring and compliance
- Building a more secure future with SIEM compliance
What is SIEM compliance?
Security information and event management (SIEM) is a solution that helps organizations recognize and address potential security threats and vulnerabilities before they happen and potentially disrupt business operations.
SIEM systems collect and analyze volumes of data from different applications, devices, servers, and users into a unified platform to:
- Centralizing and analyzing for greater insights into a company's security.
- Detect and identify potential security breaches in real time.
- Investigate and prioritize security incidents to reduce the time and resources required to solve these problems.
- Comply with regulatory and industry-specific security standards and frameworks.
SIEM solution's key components are log management, event correlation, monitoring, and incident response. SIEM solutions use Artificial Intelligence to help achieve these kinds of analyses and strengthen a business's cybersecurity practices and strengths.
Why companies need SIEM compliance
As companies grow and store more data, monitoring, identifying, and reporting security incidents can become challenging, increasing the risk of breaches and making security audits harder to pass.
Companies need SIEM for the following reasons.
Meet regulatory requirements
GDPR, HIPPA, SOX, CCPA, and other regulatory bodies require organizations to log user activities, system access, and security events. SIEM, therefore, helps meet these requirements and shows companies have accountability by verifying that they are following the established policies and security measures required when handling data.

Improve incident response
SIEM compliance requirements must have protocols to detect, assess, and mitigate security threats. As a result, businesses can take immediate action to contain security breaches and prevent threats such as ransomware.
For example, in 2024, if a company was part of a data breach or security incident, the average time to identify this was 318 days, according to a recent data breach report by IBM. The average cost of these breaches also reached $4.88 million.
Therefore, Companies need SIEM compliance to meet regulatory requirements and save their company from financial losses.
Automated reporting for audits
Businesses are often required to log and report security alerts and threats, and SIEM does this automatically to reduce the burden for businesses.
With real-time monitoring and alerts, companies can investigate any unauthorized access or other threats and investigate and eliminate the threat before it leads to a data breach or compliance violation.
By automating this process, businesses can provide detailed reports and ensure that these reports can be delivered accurately and on time to reduce fines.
SIEM compliance requirements
SIEM compliance is built up of different components, and here are the main ones to be aware of when considering incorporating SIEM into your business.
Log collection and management
Log collection captures and provides a comprehensive record of an IT environment, such as user activities, system events, and security incidents, and centralizes all this data in one place for efficient documentation for auditing and investigation.
Logs are aggregated and formatted into common formats, such as syslog, JSON, and XML and can be employed by any of the following:
- Agents transmit log contents to the SIEM solution.
- API connections gather logs through API endpoints using API keys and are frequently employed for third-party and cloud applications.
- Application integrations handle data in different formats, extract relevant fields, and create visualizations depending on the required use cases.
- Webhooks forward data from the SIEM solution to another platform, triggered by a rule to notify users or teams of potential issues.
- Custom scripts may execute scheduled, customized scripts to collect data from source systems and transmit it to the chosen SIEM software.
Threat detection
Businesses expose themselves to cyberattacks and other data threats without a monitoring and threat detection tool. SIEM helps reduce and identify risks through real-time monitoring of unusual behavior or unauthorized access.
This helps businesses remain proactive in staying on top of potential issues and helps with broader compliance by documenting and fixing gaps in security before they become a bigger problem.
Automated alerts and notifications
Building off from threat detection, the next benefit of SIEM compliance tools is automatic and automated notifications. Having a detailed log management system becomes useless if teams aren’t notified immediately, so automating alerts allows for immediate action to take place against these potential threats:
- Multiple Failed Login Attempts
- Account Lockouts
- Suspicious User Behavior
- Malware or Virus Detection
- Unusual Network Traffic
- Data Loss or Leakage
- System or Service Downtime
- Intrusion Detection
Data retention and storage
Regulation bodies such as the GDPR require organizations to securely store logs and event data for auditing and investigating security events. Companies like Internxt Business or S3 storage can help businesses store this data. Internxt is a GDPR cloud storage provider using zero-knowledge and end-to-end encryption to guarantee all data is kept private and secure.
Reports, audits, and dashboards
After SIEM solutions gather data, the results can be accessed and translate into insights presented through pre-configured dashboards for a clear and actionable solution to security actions.
These dashboards also prove accountability and transparency regarding data handling and incident tracing, helping businesses provide verifiable proof that protocols are followed and appropriately managed.
SIEM use cases
SIEM use cases offer many advantages to businesses, such as helping meet other compliance standards, reducing cybersecurity risks, and offering maximum protection for your business to ensure business continuity and success.
GDPR compliance
GDPR cloud storage and SIEM can work together to meet regulatory requirements and protect user data. One of the mandates GDPR requires is that companies maintain records of data processing activities.
SIEM uses data minimization tools to ensure only necessary data is accessed or stored, preventing GDPR’s purpose limitation and not exposing unnecessary data to a breach.

Finally, as SIEM systems monitor user activities and access logs, any incident can be notified immediately to help prevent a data breach in real time and help businesses meet the 72-hour breach notification requirement.
PCI DSS Compliance
PCI DSS (Payment Card Industry Data Security Standard) and SIEM compliance tools help protect cardholder data for businesses that handle payment card information or any other organization that stores, processes, or transmits payment card data.
SIEM systems are helpful for these organizations in detecting and alerting them to potential breaches, unauthorized transactions, or data leaks.
Cloud security monitoring
SIEM compliance and cloud security monitoring work together to enhance the security of cloud environments. Cloud security monitoring continuously monitors the cloud infrastructure for potential security risks.
At the same time, SIEM systems collect and analyze logs, events, and security data to detect and respond to threats.
SIEM systems can integrate with cloud platforms to monitor and log activities such as access to sensitive data, configuration changes, and unusual network traffic that could impact a business's workflow, security, or reputation.
IoT threat detection
As technology evolves, so does the adoption of the Internet of Things being included in business operations, with 25 billion devices expected to be in use in 2025, increasing the number of vulnerabilities and threats for cybercriminals to target.
SIEM tools can continuously monitor these devices or potential access points, conduct behavior analysis and monitor for unusual activity that could indicate irregularities or unauthorized access so action can be taken if necessary.
Phishing prevention
Phishing and ransomware are the most common cyberattacks businesses face. SIEM tools can help prevent these by filtering and searching emails containing suspicious links, content, that have been mass-sent to employees.
If any email is considered a potential risk, it will alert the necessary party for further investigation and response.
Lateral movement prevention in networks
When hackers try to access a network, they rarely stay in one place and instead, try to move to different access points to steal data or credentials that will give them higher access to more confidential information.
By continuously monitoring entire networks, SIEM systems can block and isolate these attacks to prevent further escalation and fix the current issues before more harm is done.
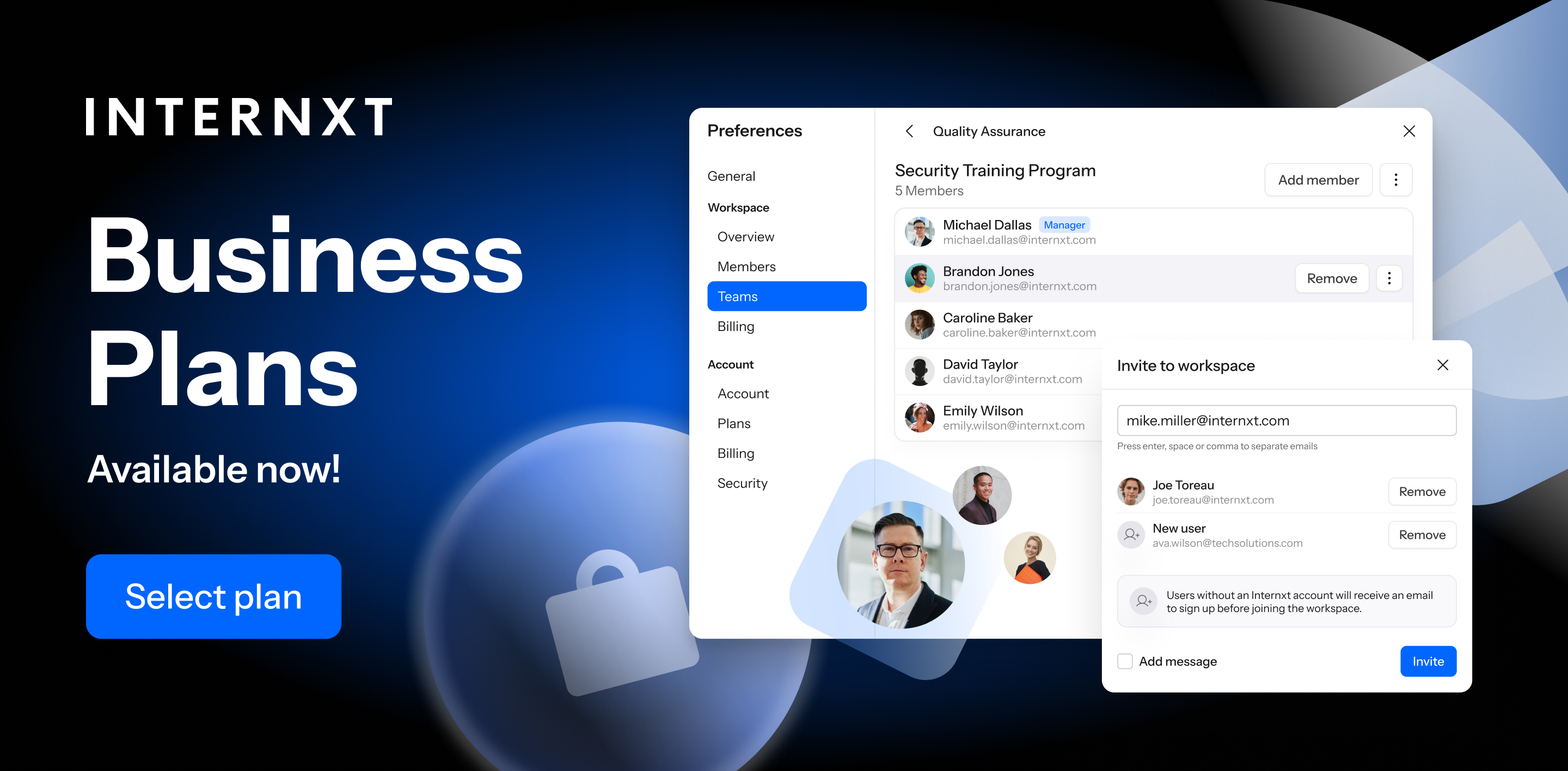
How Internxt helps with account monitoring and compliance
Internxt Drive for Business and Internxt S3 object storage have advanced features that help with GDPR compliance and real-time monitoring features to monitor for unauthorized access.
Internxt for business lets account managers easily monitor team activity with a comprehensive activity log, giving the account manager a clear view of file interactions and user access. Track who has signed in, uploaded, or modified files, giving you total control and ensuring data security across your team.
Both Internxt cloud storage also offer the encryption, security, and storage requirements needed to store and retain logs or data that organizations can store and maintain necessary for audits and compliance.
Cloud storage also ensures sensitive data is protected, while its lifecycle management features can help automate the deletion or archiving of logs according to regulatory policies so no data is stored that isn’t completely necessary.
Internxt Drive for business offers secure, encrypted cloud storage for up to 100 users, with 2TB of storage each on the Monthly or Pro plans.
Internxt S3 is the perfect AWS alternative for businesses that want to store vast data without data transfer fees or API charges.
With this storage option, businesses can get the same GDPR-compliant cloud storage, maximum security, and ultra-fast speeds at just €7/TB/month, potentially offering unlimited cloud storage for your organization.

Building a more secure future with SIEM compliance
SIEM compliance is a valuable addition that takes away the manual work of security experts and provides a reliable solution to detect, prevent, and respond to many of the emerging threats to corporate or customer data we face daily.
By incorporating SIEM systems, you can help your company build a secure future and continuously improve its security and reputation to build customer trust, save money, and stay ahead of future security risks.
To find out how Internxt can help your organization with secure, compliant, and encrypted cloud storage, with real-time monitoring and access controls, visit our website or contact us at hello@internxt.com to learn more.

